Crack Fortigate Vm64
FortiGate-VMUL FG-VMUL, FG-VMULV FortiGate-VM ‘virtual appliance’. Unlimited vCPU cores and RAM. No VDOM by default for FG-VMULV model. FortiGate-VM 6.2.2 no longer has RAM restriction on all vCPU models while prior versions still restrict RAM sizes per model. Upgrade to 6.2.2 is. From VMware Workstation we will open the FortiGate-VM64.ovf file and import it in a folder (in our example the destination is a directory located in an external storage). FortiGate VM evaluation license. We will use the evaluation license that is included by default in the FortiGate VM. What I have on this demo is FortiGate-VM64.hw04, which would run on the Fortigate’s latest firmware version 5.4. Installation of Fortigate VM version 5.0 in VMware and initial setup. Download Fortigate VM v5.0 for VMware. Fortigate-VM - Free download as PDF File (.pdf), Text File (.txt) or read online for free. Re: Crack Fortigate-vm to use free forever 2017/06/13 09:05:12 ☄ Helpful by thegiraffethatwasntpresident 2017/06/14 01:07:04 5 (1) Please do not post on this Forum requesting means to bypass product licensing. HackerTool/Crack At a glance: ID: 504291. Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been.
FortiGate VM Initial Configuration
Before you can connect to the FortiGate VM web-based manager you must configure a network interface in the FortiGate VM console. Once an interface with administrative access is configured, you can connect to the FortiGate VM web-based Manager and upload the FortiGate VM license file that you downloaded from the Customer Service & Support website.
123movies free for mac. The following topics are included in this section: Set FortiGate VM port1 IP address
- Connect to the FortiGate VM Web-based Manager
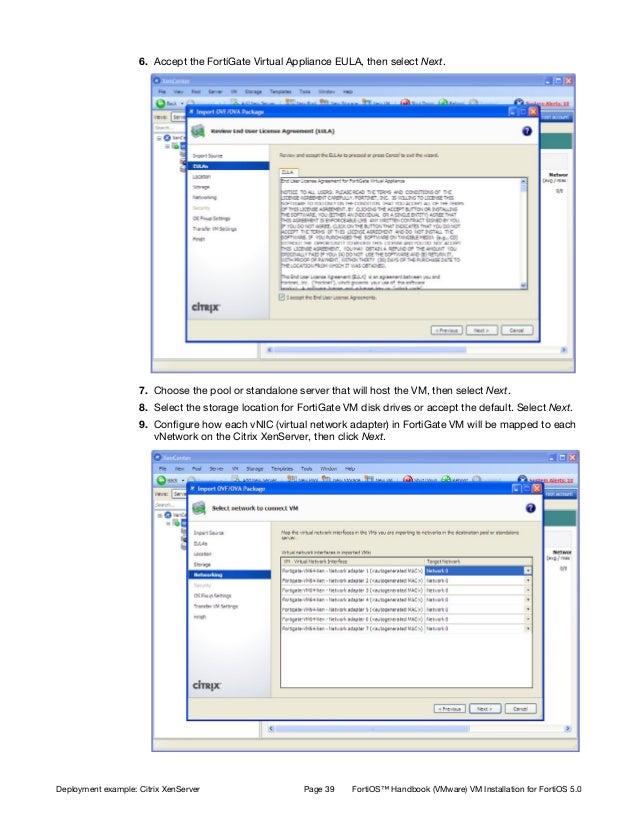
- Upload the FortiGate VM license file
- Validate the FortiGate VM license with FortiManager
- Configure your FortiGate VM
Set FortiGate VM port1 IP address
Hypervisor management environments include a guest console window. On the FortiGate VM, this provides access to the FortiGate console, equivalent to the console port on a hardware FortiGate unit. Before you can access the Web-based manager, you must configure FortiGate VM port1 with an IP address and administrative access.
To configure the port1 IP address:
1. In your hypervisor manager, start the FortiGate VM and access the console window.
You might need to press Return to see a login prompt.
Example of FortiGate VM console access:
2. At the FortiGate VM login prompt enter the username admin. By default there is no password. Just press Return.
3. Using CLI commands, configure the port1 IP address and netmask. Also, HTTP access must be enabled because until it is licensed the FortiGate VM supports only low-strength encryption. HTTPS access will not work.
For example:
config system interface edit port1
set ip 192.168.0.100 255.255.255.0 append allowaccess http
end
You can also use the append allowaccess CLI command to enable other access protocols, such as auto-ipsec, http, probe-response, radius-acct, snmp, and telnet. The ping, https, ssh, and fgfm protocols are enabled on the port1 interface by default.
4. To configure the default gateway, enter the following CLI commands:
config router static edit 1
set device port1
end
set gateway <class_ip>
You must configure the default gateway with an IPv4 address. FortiGate VM needs to access the Internet to contact the FortiGuard Distribution Network (FDN) to validate its license.
5. To configure your DNS servers, enter the following CLI commands:
config system dns
set primary <Primary DNS server>
set secondary <Secondary DNS server>
end
The default DNS servers are 208.91.112.53 and 208.91.112.52.
6. To upload the FortiGate VM license from an FTP or TFTP server, use the following CLI command:
execute restore vmlicense {ftp tftp} <VM license file name> <Server IP or FQDN> [:server port]
You can also upload the license in the FortiGate VM Web-based Manager. See Set FortiGate VM port1 IP address on page 2728.
Web–based Manager and Evaluation License dialog box
Connect to the FortiGate VM Web-based Manager
When you have configured the port1 IP address and netmask, launch a web browser and enter the IP address that you configured for port1. At the login page, enter the username admin and password field and select Login. The default password is no password. The Web-based Manager will appear with an Evaluation License dialog box.
Upload the FortiGate VM license file
Every Fortinet VM includes a 15-day trial license. During this time the FortiGate VM operates in evaluation mode. Before using the FortiGate VM you must enter the license file that you downloaded from the Customer Service & Support website upon registration.
To upload the FortiGate VM licence file:
1. In the Evaluation License dialog box, select Enter License.
You can also upload the license file via the CLI using the following CLI command:
execute restore vmlicense [ftp tftp] <filenmame string>
<ftp server>[:ftp port]
The license upload page opens.
License upload page:
2. Select Browse and locate the license file (.lic) on your computer. Select OK to upload the license file.
3. Refresh the browser to login.
Crack Fortigate Vm64 Download
4. Enter admin in the Name field and select Login. The VM registration status appears as valid in the License Information widget once the license has been validated by the FortiGuard Distribution Network (FDN) or FortiManager for closed networks.
Validate the FortiGate VM license with FortiManager
You can validate your FortiGate VM license with some models of FortiManager. To determine whether your FortiManager unit has the VM Activation feature, see Features section of the FortiManager Product Data sheet.
To validate your FortiGate VM with your FortiManager:
1. To configure your FortiManager as a closed network, enter the following CLI command on your FortiManager:
config fmupdate publicnetwork set status disable
end
2. To configure FortiGate VM to use FortiManager as its override server, enter the following CLI commands on your
FortiGate VM:
config system central-management set mode normal
set type fortimanager
set fmg <IPv4 address of the FortiManager device>
set fmg-source-ip <Source IPv4 address when connecting to the FortiManager device>
set include-default-servers disable
set vdom <Enter the name of the VDOM to use when communicating with the FortiManager device>
end
3. Load the FortiGate VM license file in the Web-based Manager. Go to System > Dashboard > Status. In the License Information widget, in the Registration Status field, select Update. Browse for the .lic license file and select OK.
4. To activate the FortiGate VM license, enter the following CLI command on your FortiGate VM:
execute update-now
5. To check the FortiGate VM license status, enter the following CLI commands on your FortiGate VM:
get system status
The following output is displayed:
Crack Fortigate Vm64 3
Version: Fortigate-VM v5.0,build0099,120910 (Interim) Virus-DB: 15.00361(2011-08-24 17:17)
Extended DB: 15.00000(2011-08-24 17:09) Extreme DB: 14.00000(2011-08-24 17:10) IPS-DB: 3.00224(2011-10-28 16:39)
FortiClient application signature package: 1.456(2012-01-17 18:27) Serial-Number: FGVM02Q105060000
License Status: Valid
BIOS version: 04000002
Log hard disk: Available Hostname: Fortigate-VM Operation Mode: NAT
Current virtual domain: root
Max number of virtual domains: 10
Virtual domains status: 1 in NAT mode, 0 in TP mode
Virtual domain configuration: disable
FIPS-CC mode: disable Current HA mode: standalone Distribution: International Branch point: 511
Release Version Information: MR3 Patch 4
System time: Wed Jan 18 11:24:34 2012
diagnose hardware sysinfo vm full
The following output is displayed: UUID: 564db33a29519f6b1025bf8539a41e92 valid: 1
status: 1
code: 200 (If the license is a duplicate, code 401 will be displayed)
warn: 0 copy: 0 received: 45438 warning: 0
recv: 201201201918 dup:
Configure your FortiGate VM
nce the FortiGate VM license has been validated you can begin to configure your device. You can use the Wizard located in the top toolbar for basic configuration including enabling central management, setting the admin password, setting the time zone, and port configuration.
For more information on configuring your FortiGate VM see the FortiOS Handbook at http://docs.fortinet.com.
Having trouble configuring your Fortinet hardware or have some questions you need answered? Check Out The Fortinet Guru Youtube Channel! Want someone else to deal with it for you? Get some consulting from Fortinet GURU!
Don't Forget To visit the YouTube Channel for the latest Fortinet Training Videos and Question / Answer sessions!
- FortinetGuru YouTube Channel
- FortiSwitch Training Videos
FortiGate VM Overview Page 8 VM Installation for FortiOS 5.0 FortiGate VM. After the trial license expires, functionality is disabled until you upload a license. Fortigate-vm - download at 4shared. Fortigate-vm is hosted at free file sharing service 4shared. Fortigate Vm License Key Fortigate Vm License Key is a software selection with 90 downloads.
Home > Online Help
FortiGate VM models and licensing
Fortinet offers the FortiGate VM in five virtual appliance models determined by license. When configuring your FortiGate VM, be sure to configure hardware settings within the ranges outlined below. Contact your Fortinet Authorized Reseller for more information.
FortiGate VM model information
| Technical Specification | FG-VM00 | FG-VM01 | FG-VM02 | FG-VM04 | FG-VM08 |
|---|---|---|---|---|---|
| Virtual CPUs (min / max) | 1 / 1 | 1 / 1 | 1 / 2 | 1 / 4 | 1 / 8 |
| Virtual Network Interfaces (min / max) | 2 / 10 | ||||
| Virtual Memory (min / max) | 1GB / 1.5GB | 1GB / 2GB | 1GB / 4GB | 1GB / 6GB | 1GB /12GB |
| Virtual Storage (min / max) | 32GB / 2TB | ||||
| Managed Wireless APs (tunnel mode / global) | 32 / 32 | 32 / 64 | 256 / 512 | 256 / 512 | 1024 / 4096 |
| Virtual Domains (default / max) | 1 / 2 | 10 / 10 | 10 / 25 | 10 / 50 | 10 / 250 |
| There may be times the min/max values can change. An example for this is when the maximum memory for FG-VM00 changed between 5.2 and 5.4 from 1 GB to 1.5 GM. If that is the case, the settings for the VM will have to be manually changed to accommodate the new parameters. |
After placing an order for FortiGate VM, a license registration code is sent to the email address used on the order form. Use the registration number provided to register the FortiGate VM with Customer Service & Support and then download the license file. Once the license file is uploaded to the FortiGate VM and validated, your FortiGate VM appliance is fully functional.
The Clash Discography 12 cd mp3 192 kbps 1014.18 MB The Clash Discography 12 cd mp3 192 kbps 1014.18 MB. The clash discography torrent.
| The number of Virtual Network Interfaces is not solely dependent on the FortiGate VM. Some virtual environments have their own limitations on the number of interfaces allowed. As an example, if you go to https://docs.microsoft.com/en-us/azure/virtual-network/virtual-networks-multiple-nics, you will find that Azure has its own restrictions for VMs, depending on the type of deployment or even the size of the VM. |
FortiGate VM evaluation license
FortiGate VM includes a limited embedded 15-day trial license that supports:
- 1 CPU maximum
- 1024 MB memory maximum
- low encryption only (no HTTPS administrative access)
- all features except FortiGuard updates
You cannot upgrade the firmware, doing so will lock the Web-based Manager until a license is uploaded. Technical support is not included. The trial period begins the first time you start FortiGate VM. After the trial license expires, functionality is disabled until you upload a license file.
Copyright © 2018 Fortinet, Inc. All Rights Reserved. Terms of Service Privacy Policy Plugin bcc luma key sony vegas download.
Anyone can Access FortiOS SSH Backdoor
Proof-of-Concept Exploit Code is Available Online
Fortinet Response on the Issue
Fortigate Vm License
Fortigate Vm Licence Crack
'This was not a 'backdoor' vulnerability issue but rather a management authentication issue. The issue was identified by our Product Security team as part of their regular review and testing efforts.'